This is the blog post series related to OverTheWire Wargames which basically is my attempt to challenge myself and play some Wargames as suggested by CTF Field Guide.
This specific sub series is about the Bandit Wargame from OverTheWire community:
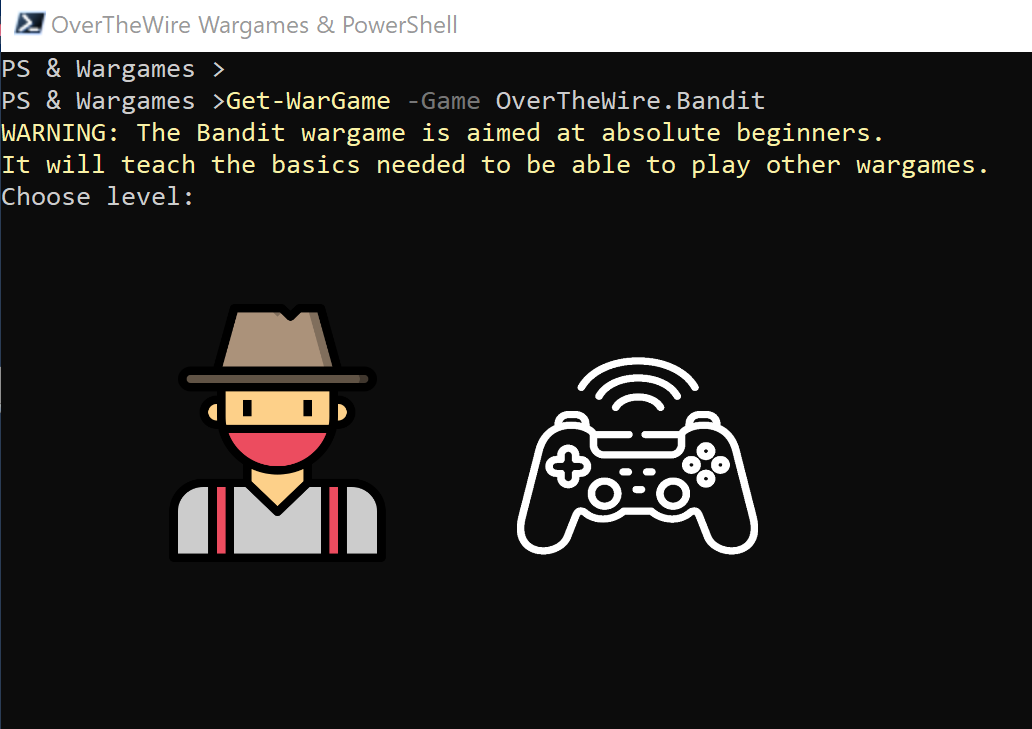
The Bandit wargame is aimed at absolute beginners. It will teach the basics needed to be able to play other wargames.
Disclaimer: I respect the rules and will not post full write up of my approach/solution to complete the challenge. I will be providing general overview of the level and key command(s) that where used to complete it.
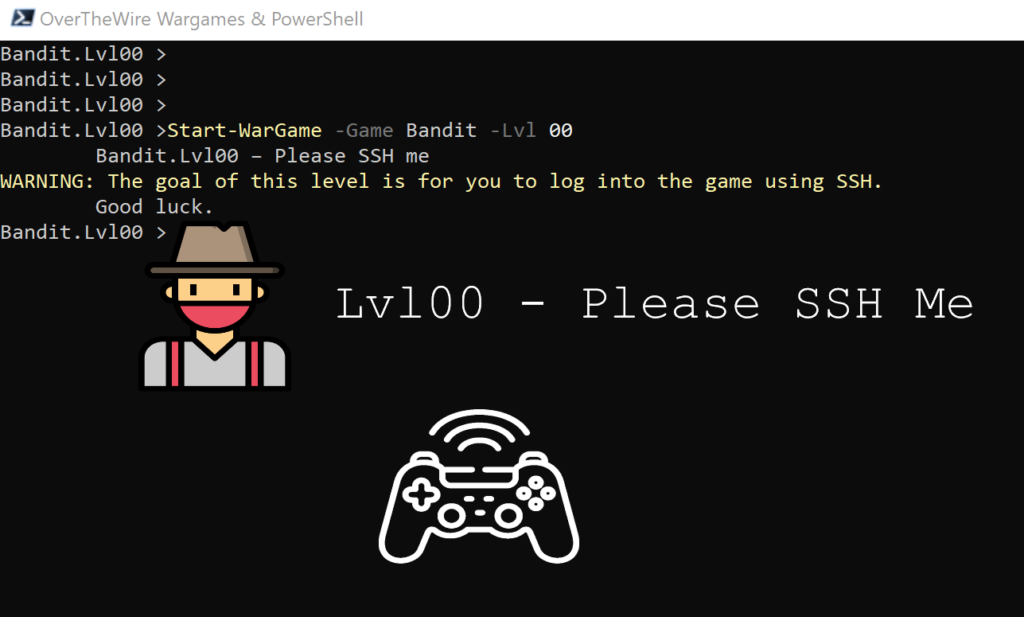
Lvl 00 – Please SSH me
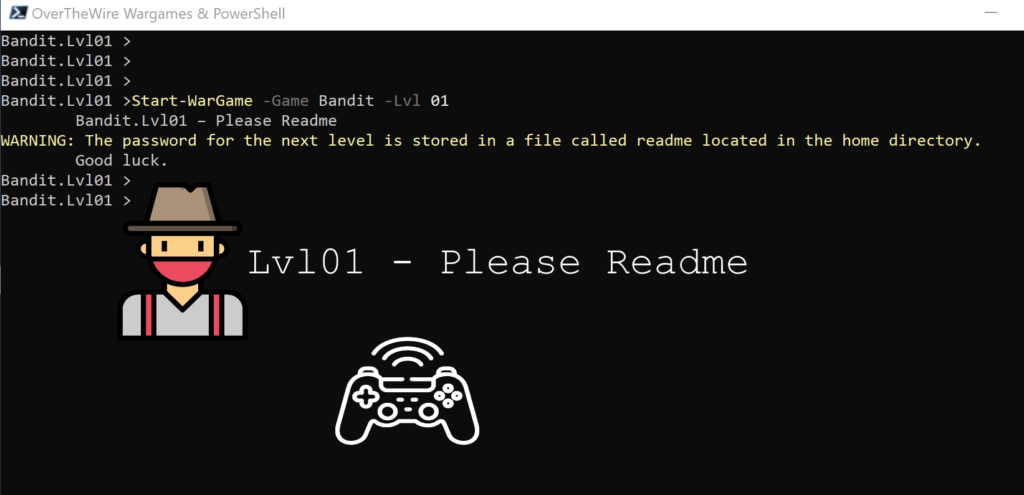
Lvl 01 – Please Readme
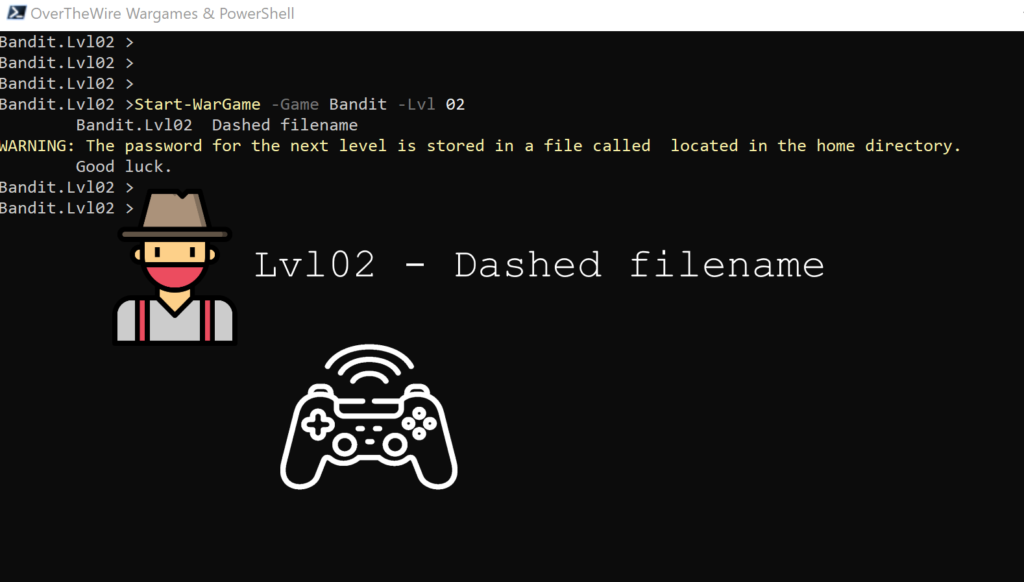
Lvl02 – Dashed filename
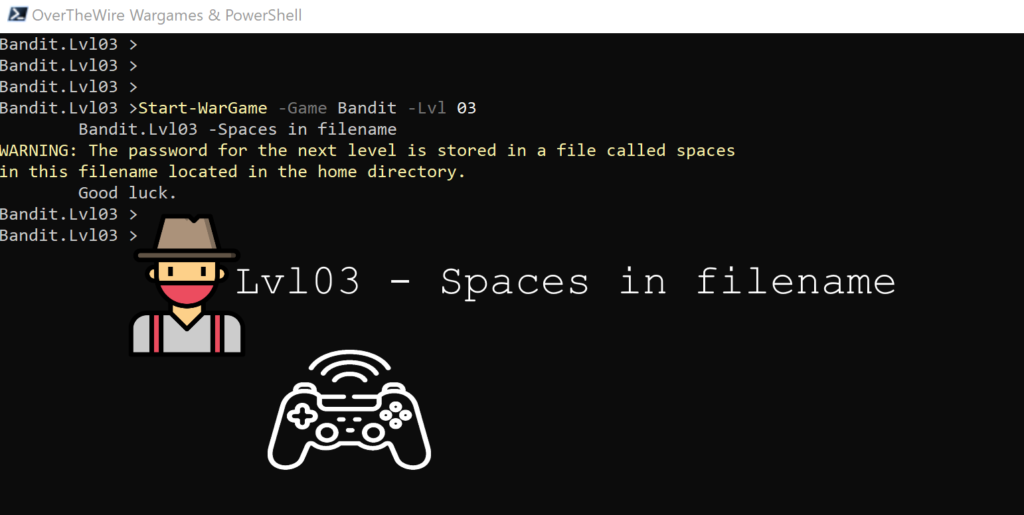
Lvl03 – Spaces in filename
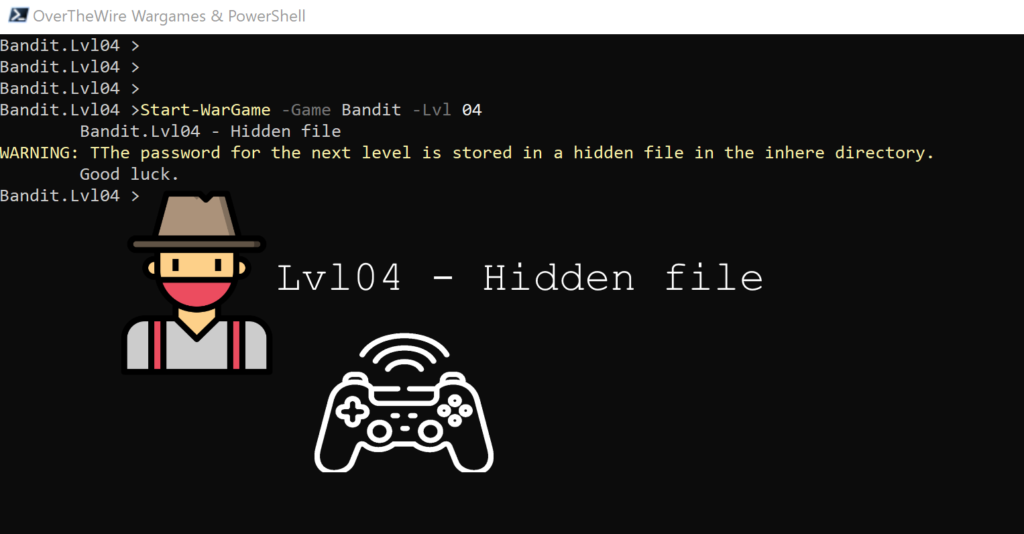
Lvl 04 – Hidden file
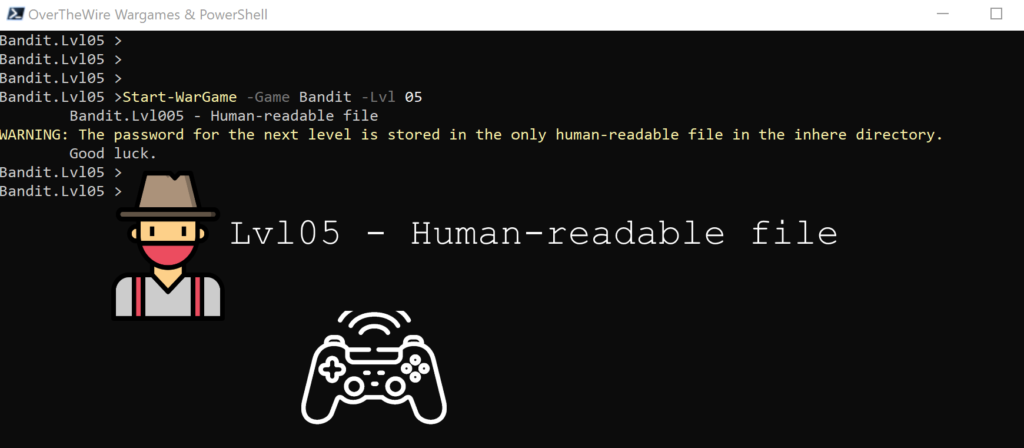
Lvl 05 – Human-readable file
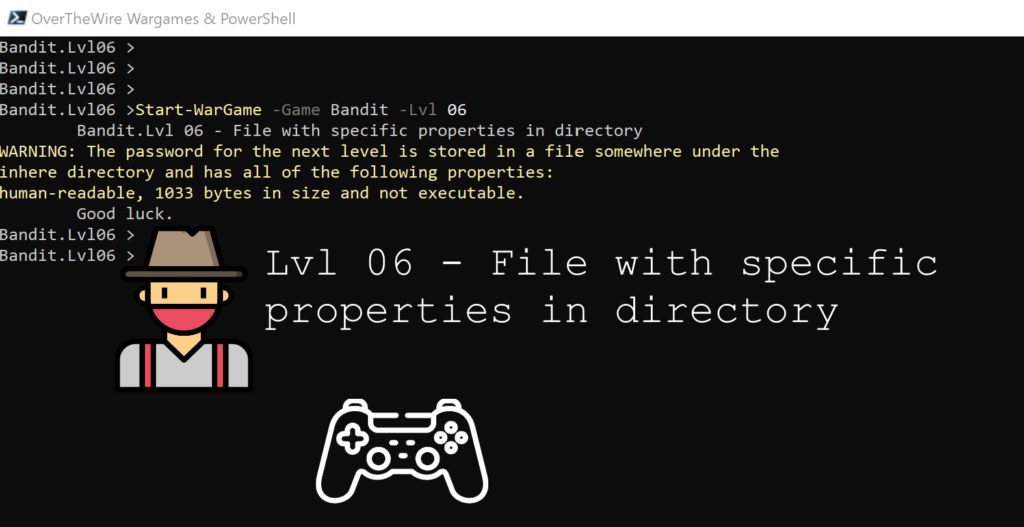
Lvl 06 – File with specific properties in directory
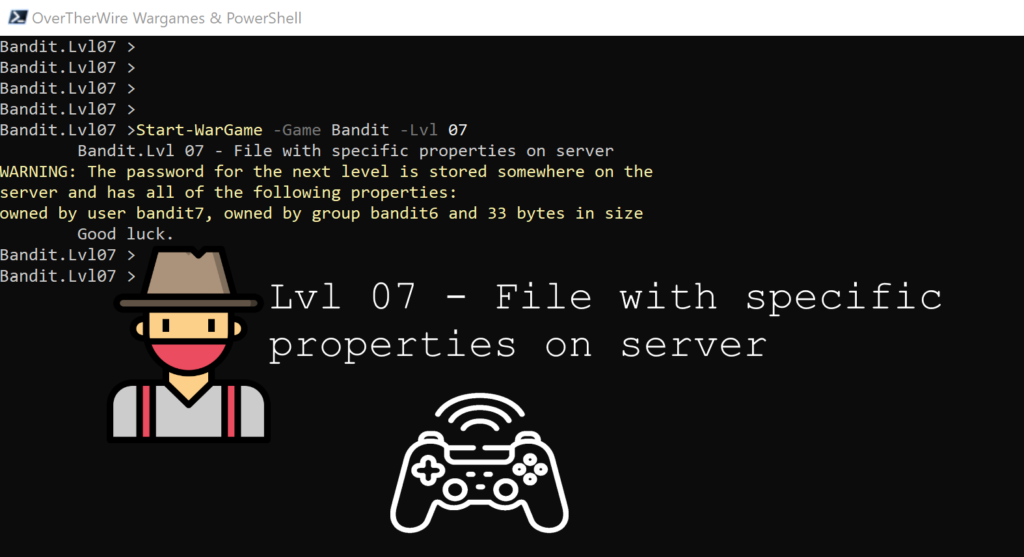
Lvl 07 – File with specific properties on server
Lvl 08 – millionth data
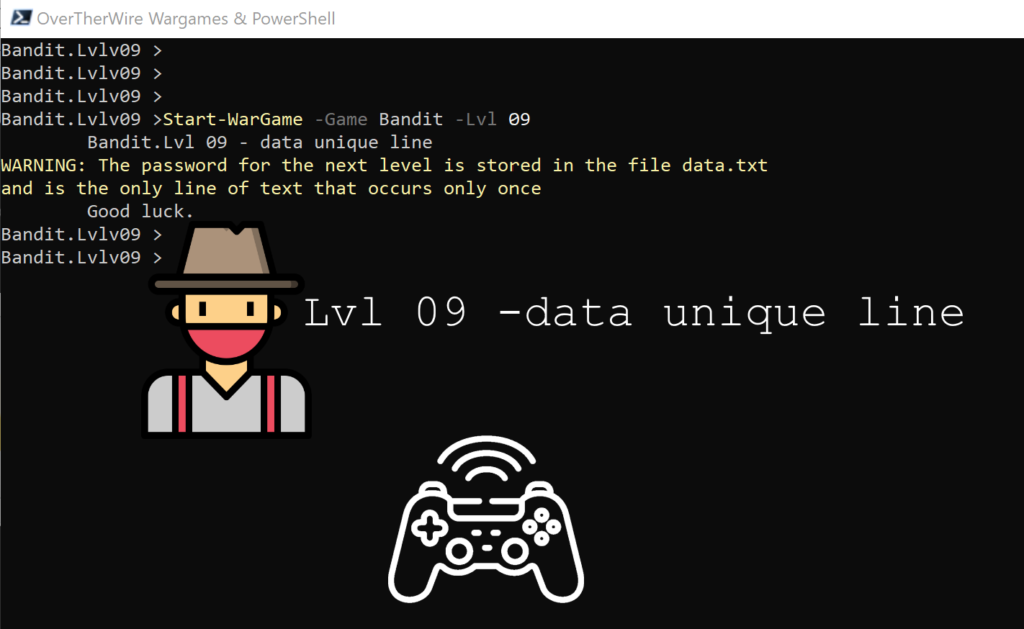
Lvl 09 – data unique line
Lvl10 – data equal signs
Lvl11 – base64 data
Lvl12 – data rotated by 13
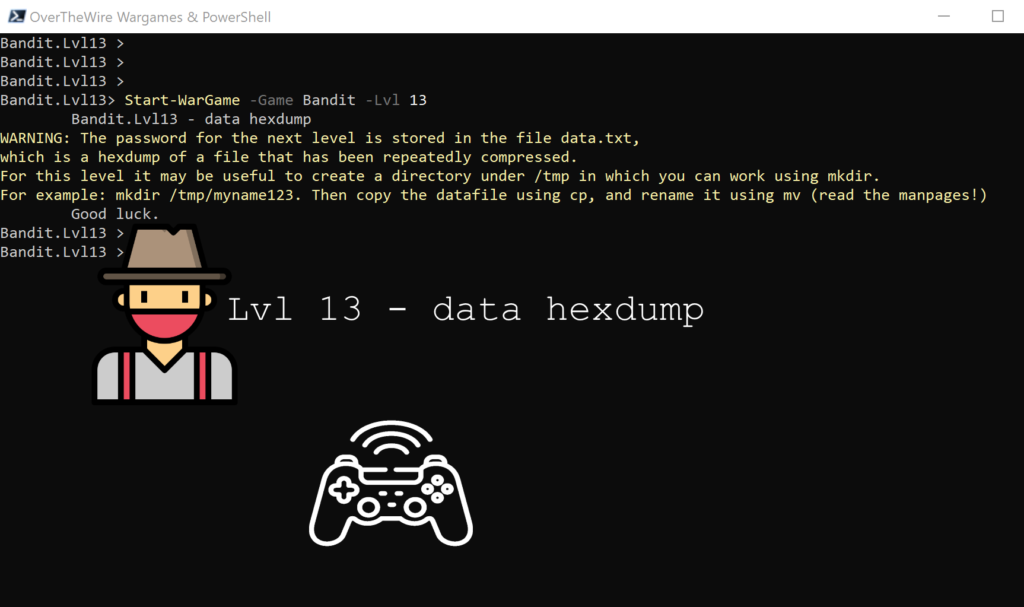
Lvl13 – data hexdump
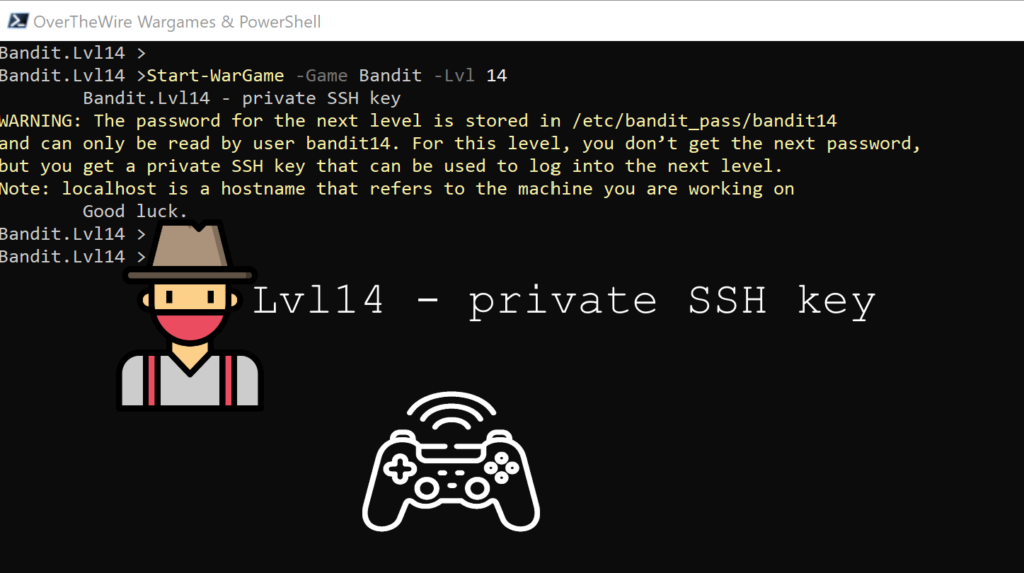
Lvl14 – private SSH key
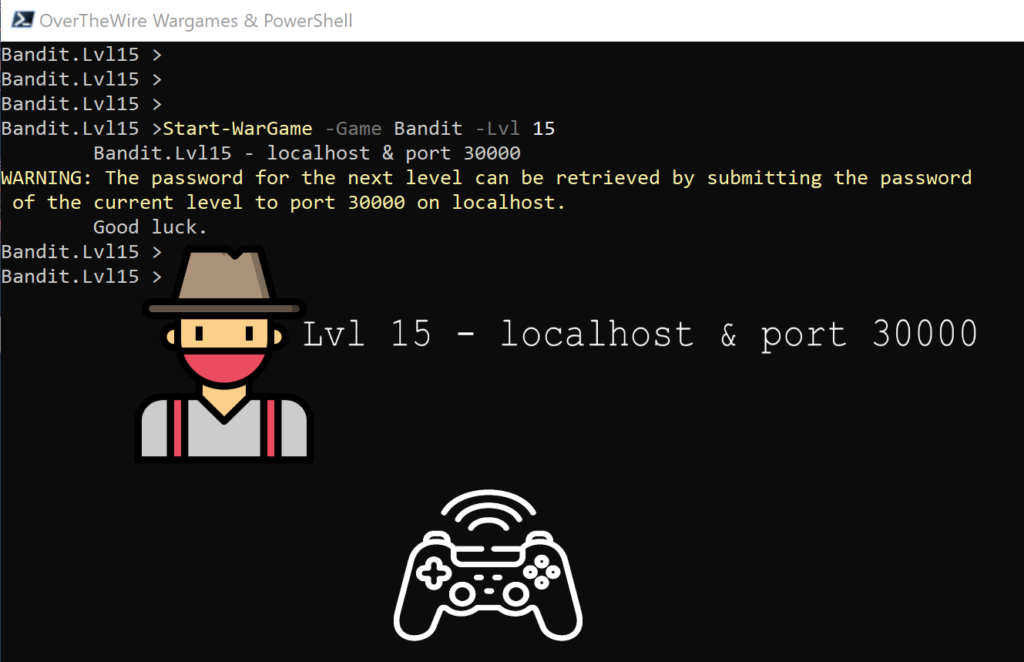
Lvl15 – localhost & port 30000
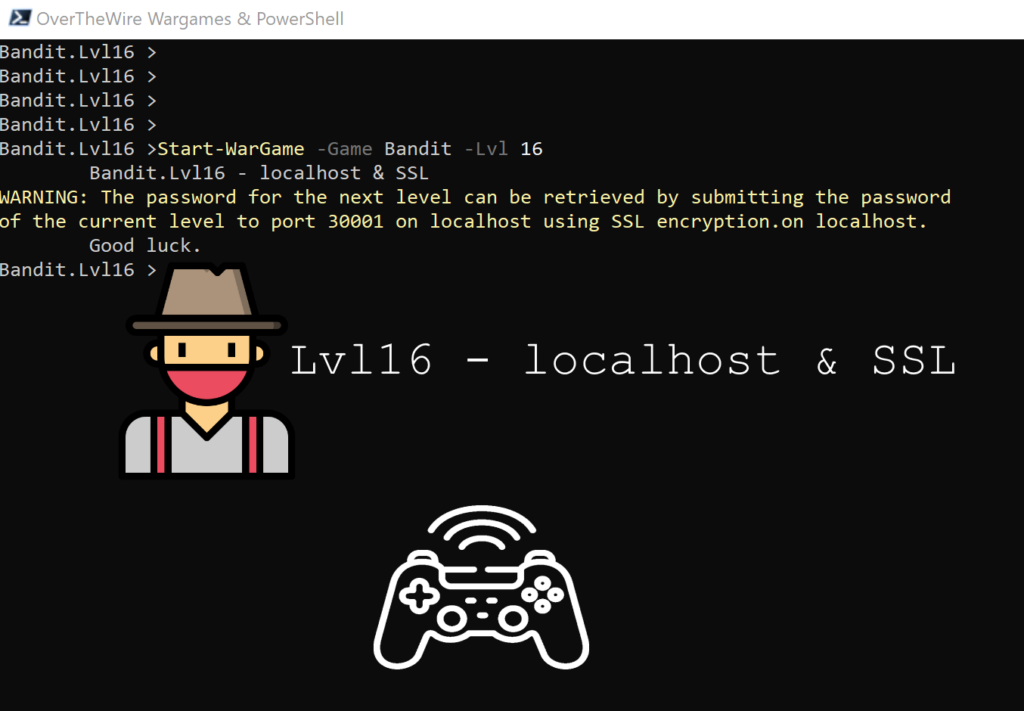
Lvl16 – localhost & SSL
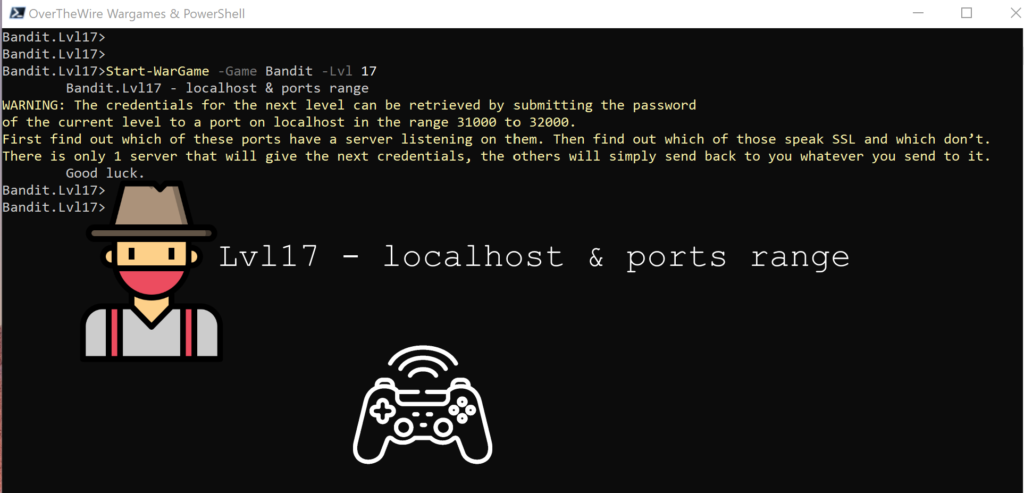
Lvl17 – localhost & ports range
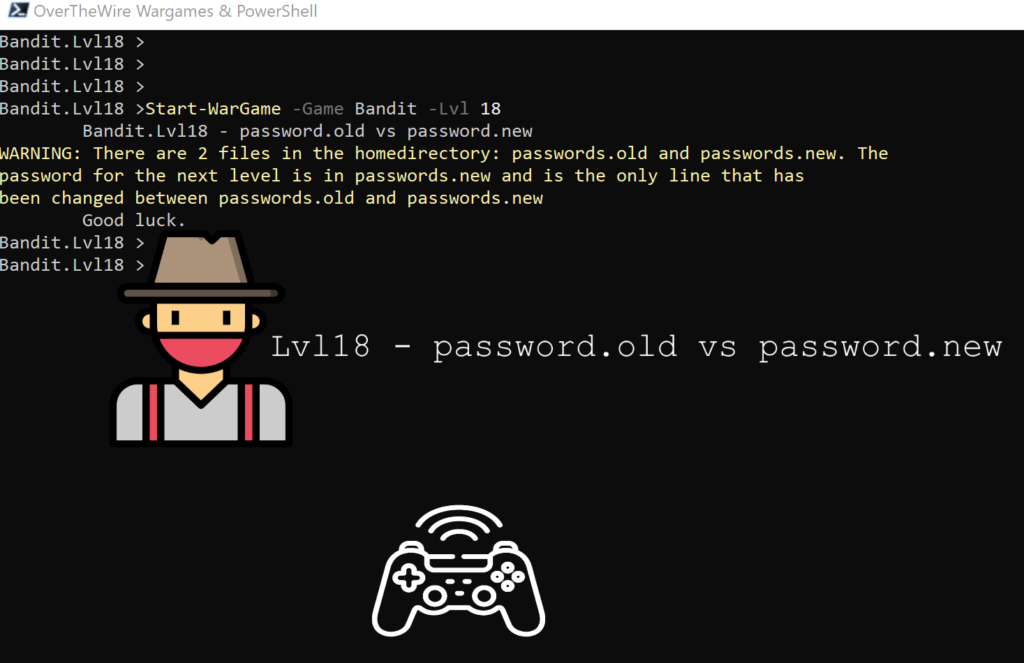
Lvl18 – password.old vs password.new
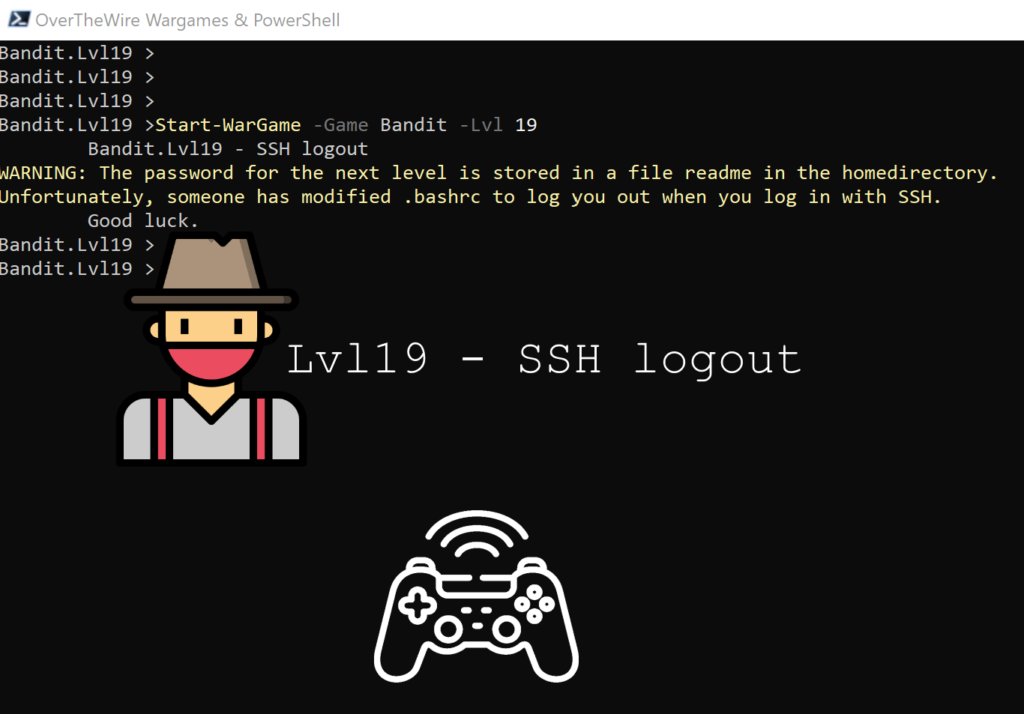
Lvl19 – SSH logout
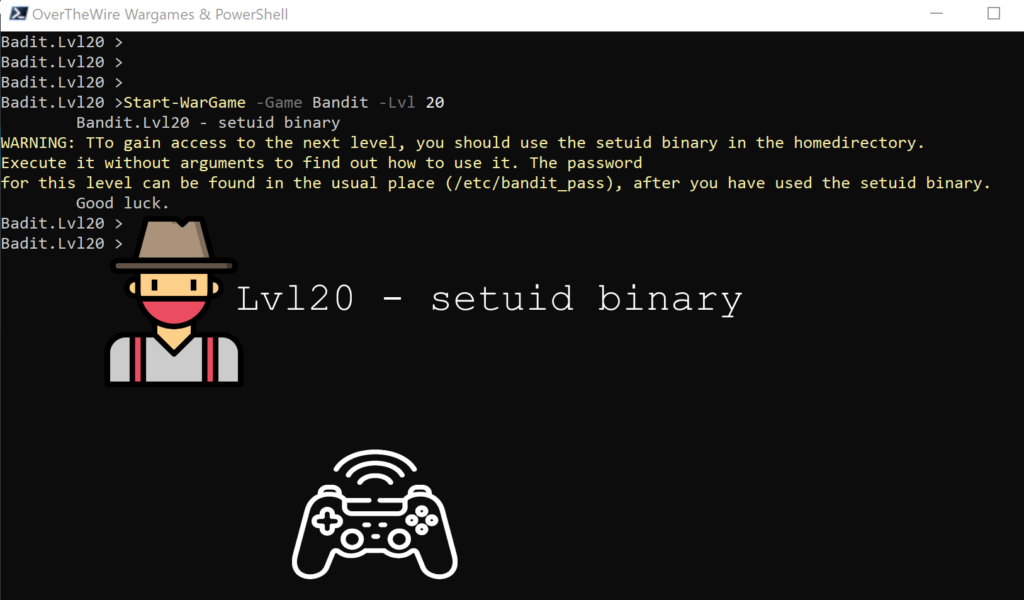
Lvl20 – setuid binary
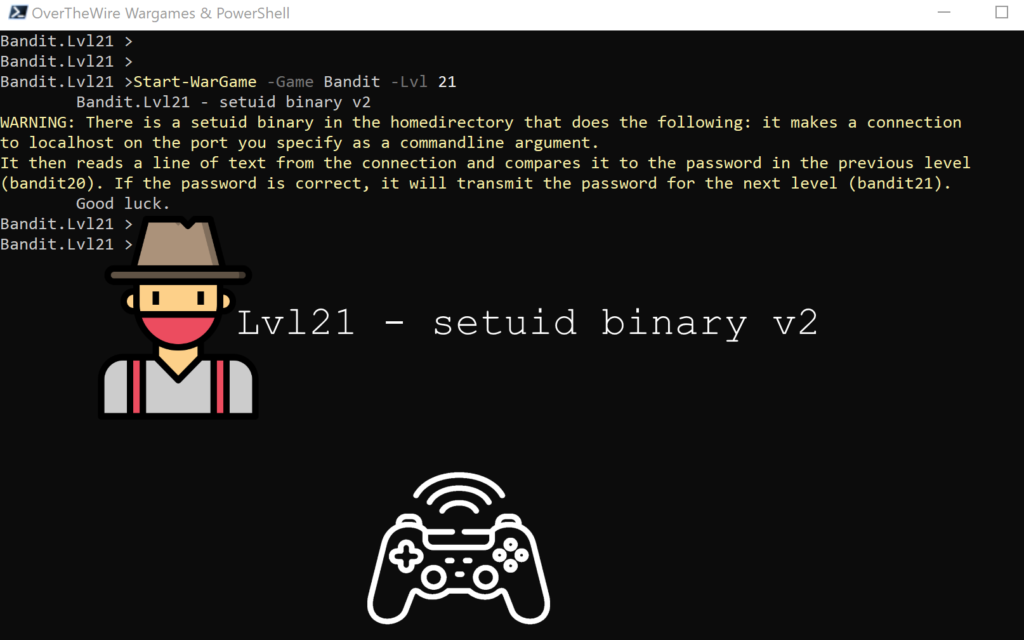
Lvl21 – setuid binary v2
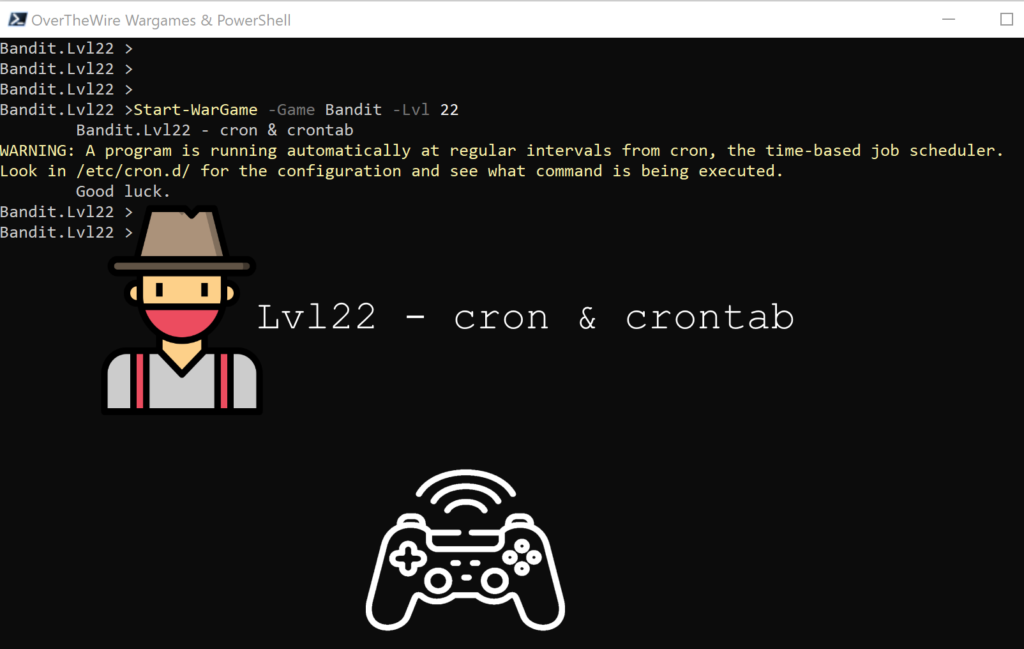
Lvl22 – cron & crontab
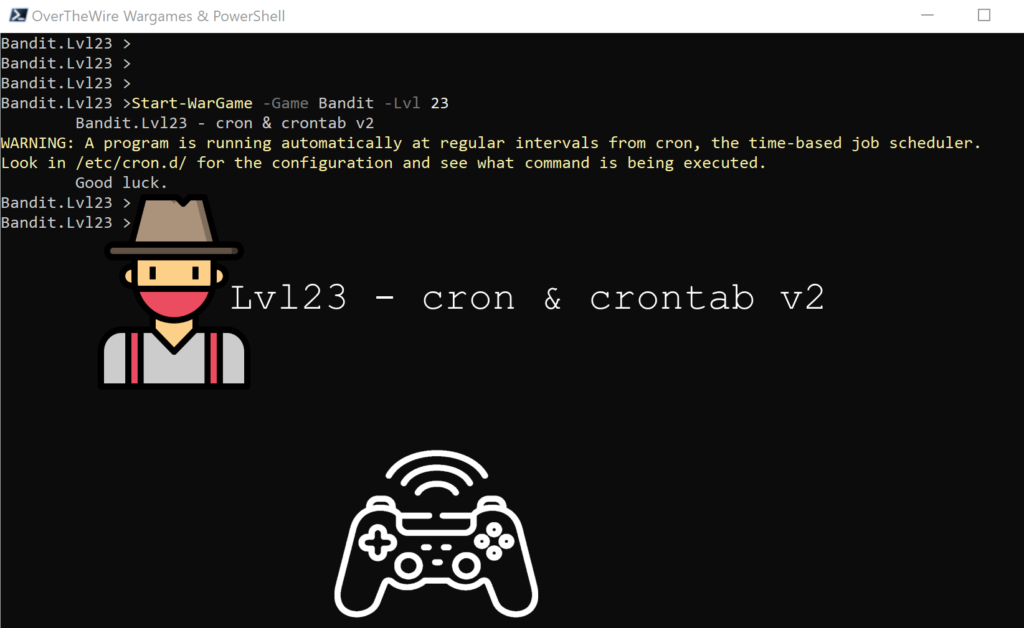
Lvl23 – cron & crontab v2
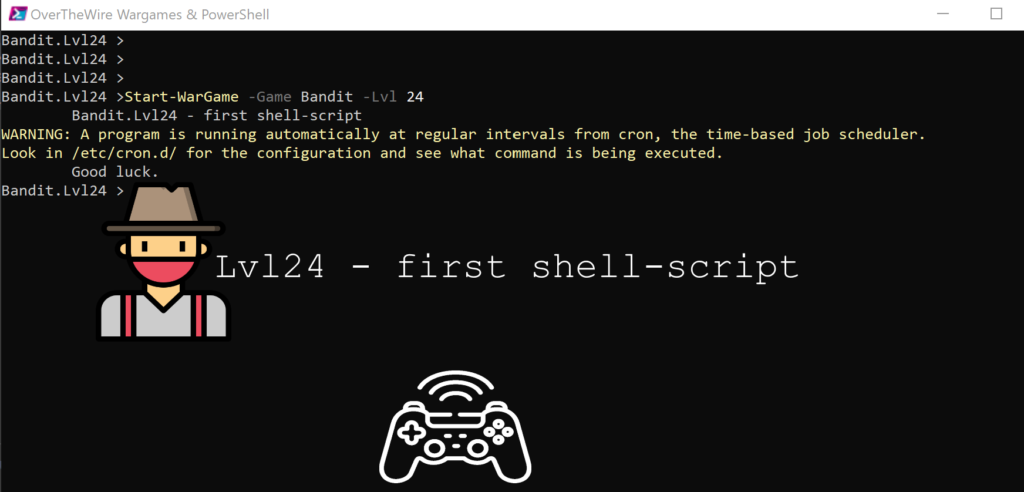
Lvl24 – first shell-script
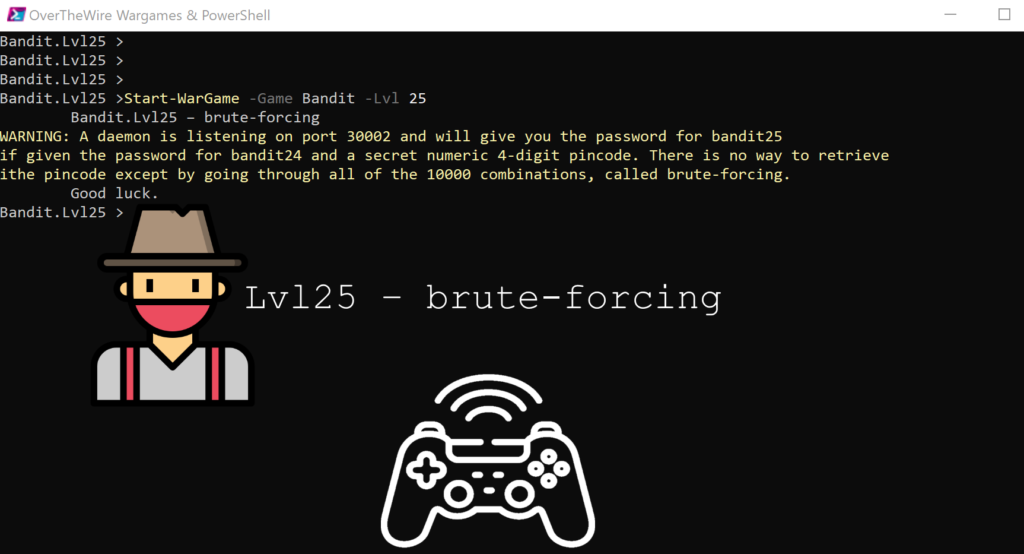
Lvl25 – brute-forcing
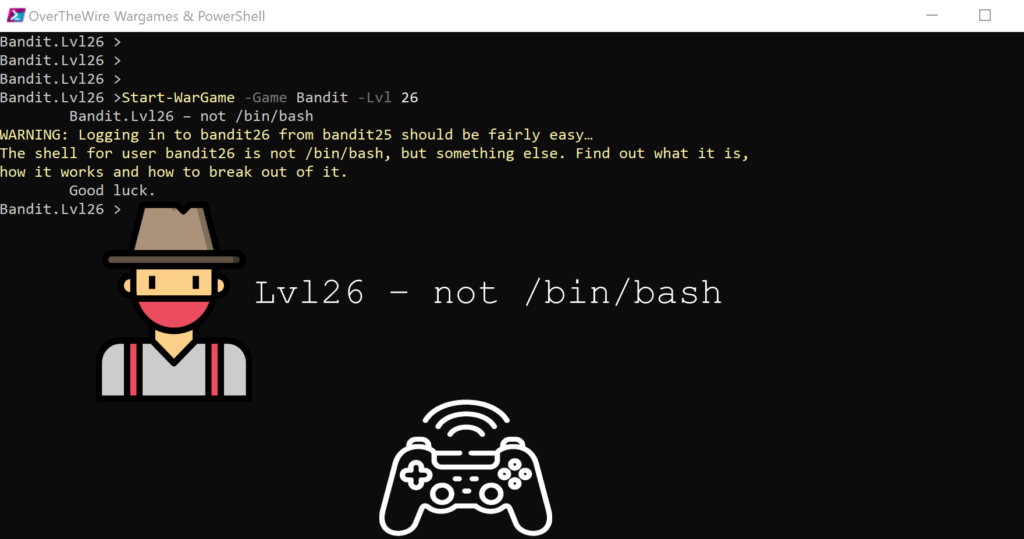
Lvl26 – not /bin/bash
Lvl27 – grab the password
Lvl28 – git repository
Lvl29 – git repository v2
Lvl30 – git repository v3
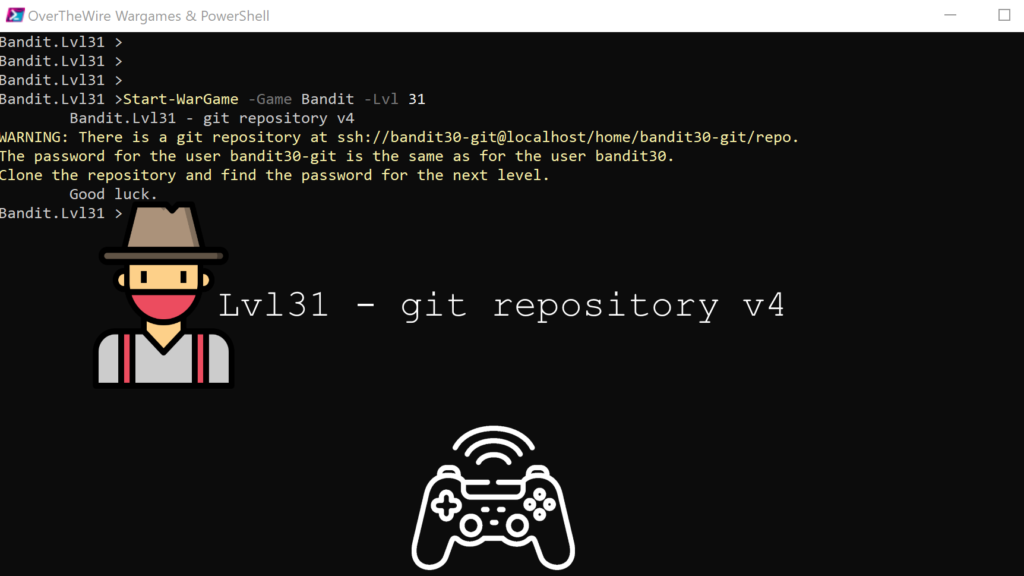
Lvl31 – git repository v4
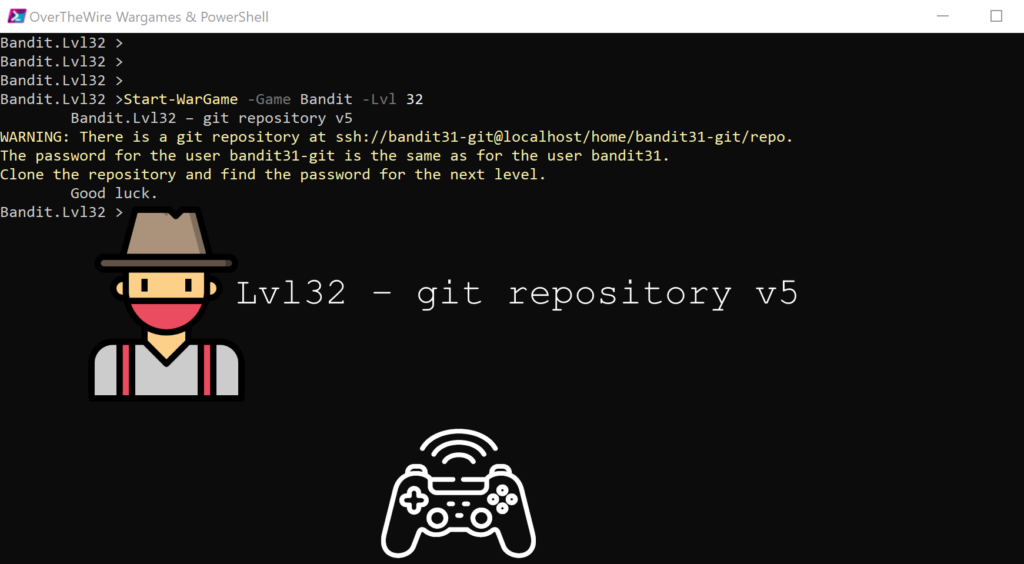
Lvl32 – git repository v5
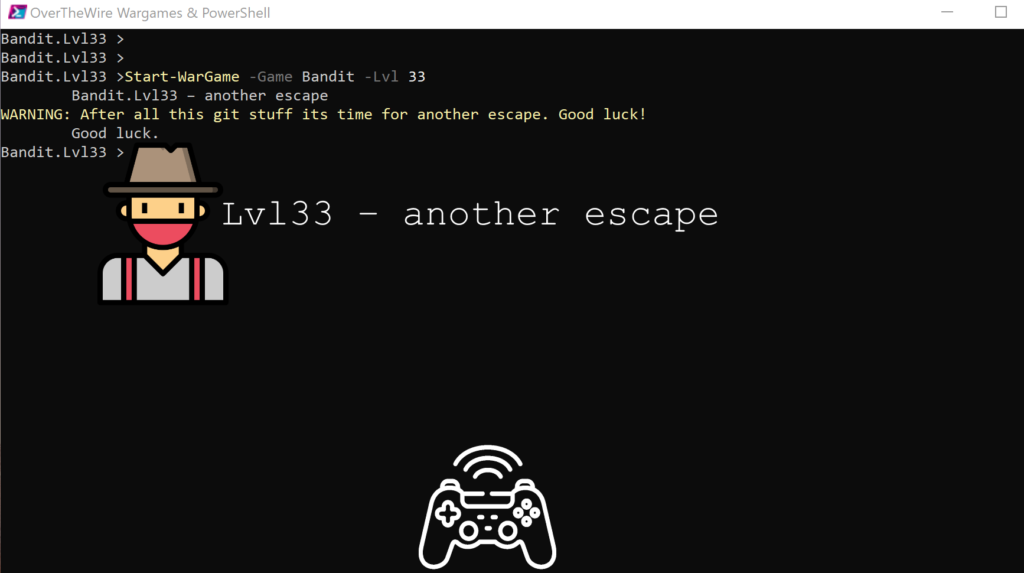
Lvl33 – another escape
Read short summary about Bandit Wargame.
Thanks a lot for reading.

Icons made by surang & Freepik from www.flaticon.com.